
The introduction to Trustwave’s latest Global Security Report said it best - “Compromises are nothing new, of course, but 2014 just felt different.” Many called it the “Year of the Data Breach.” Many more were affected directly, with billions of personal records being compromised. But maybe most importantly, 2014 thrust data security into the public eye, forcing merchants, financial institutions, government and everyone in between to place a higher priority on breach prevention and detection.
Trustwave’s report provides a unique overview of the global security landscape, what trends emerged over the past year, and what the payments industry should keep an eye on moving forward.
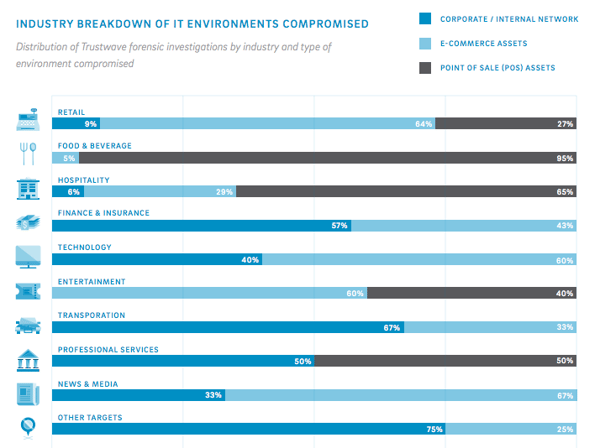
The Types of Industries Being Compromised and How
Of the nearly 600 breaches investigated by Trustwave, 58% of them occurred at retail or food and beverage businesses. Retail businesses specifically saw an 8% increase year over year. With 12% of the compromises, the hospitality industry rounded out the top three.
Ecommerce and point-of-sale (POS) environments dominated the areas that saw the most compromises, with 42% and 40%, respectively. Internal corporate networks, comparatively, were responsible for only 18% of breaches. Unsurprisingly, ecommerce environments were responsible for 64% of all retail breaches, while POS environments claimed responsibility for 95% of all food and beverage breaches. Internal corporate networks were more at fault in finance, insurance and transportation business compromises.
Compromised Environments by Location
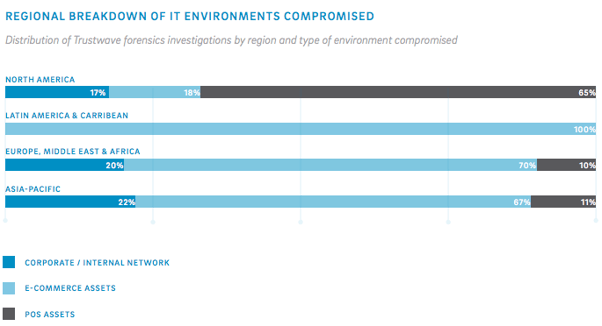
Given the upcoming EMV liability shift, it’s especially interesting to look at these compromises by region, to contrast the types of compromises seen by the United States against the types of compromises seen in areas like Europe, which have been EMV compliant for decades.
Not surprisingly, the U.S. suffers from an overwhelmingly large number of POS environment compromises compared to every other region listed on the report. In every other location, breaches are dominated by compromised ecommerce environments, which is consistent with previous studies we’ve recapped on EMV and the resulting shift in fraudulent activity.
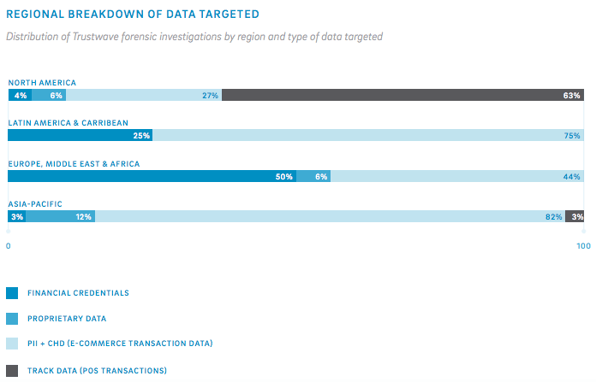
The Types of Information Being Stolen
Reversing the trend from 2013, fraudsters have shifted back to stealing more payment card data. In cases where the type of information being stolen could be identified, almost 50% of the time it was payment card data. Trustwave investigators also noted a double-digit increase in the amount of track data being stolen from POS systems. Presumably, this will see a decline next year as the EMV implementation moves forward.
This data broken down by region mirrors the regional breakdowns we covered above, with POS track data information being stolen primary in North America, with the other regions primarily suffering from ecommerce data compromises.
Breach Detection
Like previous years, the overwhelming majority of victims (81%) did not detect the breach themselves. So, who’s catching them first? In Trustwave’s investigations, 58% were initially detected by merchant banks, the card networks or regulatory bodies, though law enforcement showed a greater presence in breach detection, discovering 12% of the compromises covered in this report.
The average time it took from initial intrusion to detection of a compromise spanned a range of one day to 4.5 years, though the average was 188 days (6.25 months), a 40% increase over 2013’s average of 134 days.
The median and much more typical detection time is significantly lower at 86 days, which stayed almost the same from the previous year. What’s more interesting though, is the disparity in days to detection between companies who caught the compromise themselves (or through a provider who can do it on their behalf) vs companies whose compromise was caught externally. It’s an almost 100 day difference between the two, with companies who caught the compromise themselves looking at a median detection to intrusion time of about 10 days.
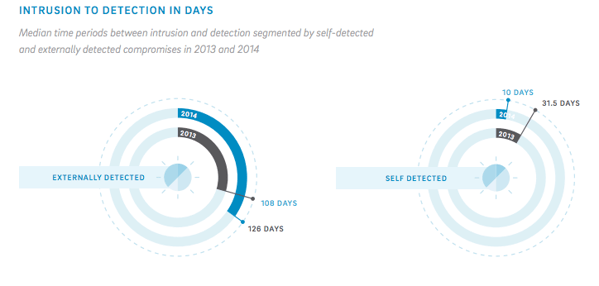
Organizations that know what they’re looking for, and can either hire in-house talent or source a managed security provider to detect breaches on their behalf unsurprisingly have a strong edge in catching compromises faster and containing them more effectively.
To learn more about Rippleshot’s breach detection and fraud analytics capabilities, visit our Knowledge Center.


