It’s been nearly a year since the Federal Financial Institutions Examinations Council (FFIEC) debuted the Cybersecurity Assessment Tool, commonly known in the industry as the CAT. At last week’s ABA Risk Management Conference, we learned a ton about the tool’s voluntary nature, how it compares to existing cybersecurity assessments, and how banks are passing the regulatory scrutiny onto their own vendors and third-party providers.
How the CAT Works
As we’ve covered in a previous article on cybersecurity regulation, the FFIEC is a federal interagency body responsible for creating standard federal assessments and examinations for all financial institutions. The CAT is the latest assessment to come from this group, and can be broken down into two primary parts:
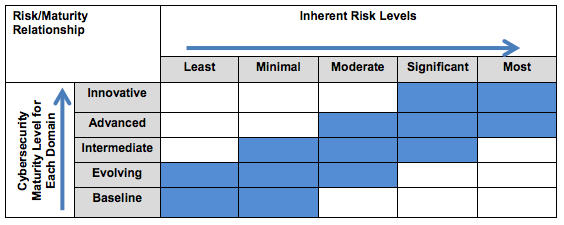
- The Risk Profile Assessment, which is a series of questions that financial institutions must answer about their own internal operations, which then leads to the determination of an inherent risk profile - from least to most.
- The Cybersecurity Maturity Guidelines - A set of cybersecurity recommendations, laid out by risk profile, that escalate in terms of requirements, as the risk profile increases.
The relationship between the two parts of the assessment is clearly outlined by the graphic below.
Voluntary? Or Not Really
As Daniel Goldstein of Treliant Risk Advisors said to the ABA group last week, “Regulators expect financial institutions to have a robust cybersecurity program.” He noted that the FDIC, Federal Reserve, and OCC are all planning to use the CAT in their exams, which certainly puts the voluntary nature in question. Even some state regulators (Texas and Massachusetts were specifically called out) are “basically requiring it,” according to panel participants.
Of the three financial institutions represented on the panel - Summit Bank NA, TowneBank and Comerica Bank - all representatives said they were asked about their CAT results by their examiner.
And for larger institutions, the expectations are even higher. Banks that are $15B or above in assets are being expected by regulators to discover emerging risks. A recent item that has the attention of many institutions is the Dwolla CFPB penalty for misleading data security statements.
What About the NIST Framework?
While no one on the panel had specific experience substituting the NIST for the CAT, since they had all completed the CAT, they still assumed that for the time being, examiners would accept NIST results. They specifically cited that examiners know how to translate NIST statements and results to their counterparts in the CAT, which is publicly available here.
One thing to keep in mind is that the CAT covers areas that the NIST does not, and some of the maturity levels of the NIST do not meet baseline in the CAT, and will need to be addressed.
Managing Third Party Data Risks
All of the bankers on the panel expressed the importance of pushing CAT guidelines out to their vendors and other third party service providers. Suppliers are notoriously behind financial institutions in areas of security and compliance, and are always scrambling to catch up, panelists mentioned.
Industry leaders FIS, Fiserv and Jack Henry were not immune from this conversation, as many wondered if they could or should rely on these processing powerhouses to be handling cybersecurity threats as seriously as banks are. “They’re probably not in as good of a position as you think,” one of the panelists said.
Curious how Rippleshot Sonar addresses some of the guidelines in the CAT? Check out our document below: