So much has happened in the Target data breach story, it's hard to keep it all straight. We've been compiling a detailed timeline of the breach, the fallout, and more details about the actual malware attack.
Update: With Businessweek's latest cover story on the Target data breach, we now know that computer security firm, FireEye, detected the breach on November 30th, before the data was transmitted off Target's network. Leading to Target's security team being notified regarding the alerts prior to the story breaking.
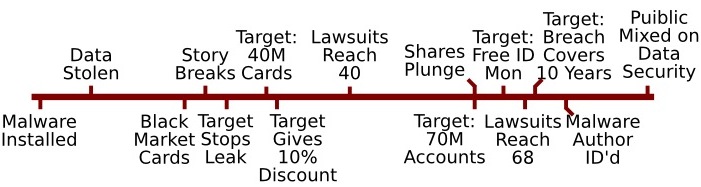
Nov 27th: Malware Installed
Beginning on the Wednesday before Black Friday, malware was first installed in Target's US environment. The malware, eventually identified by Symantec as Reedum, is a descendent of BlackPOS, a POS malware available on various cybercrime forums (more on Reedum/BlackPOS below). Krebs On Security reports that a source close to the investigation claimed that none of the 40+ commercial antivirus tools used to scan malware at Virus Total, as of Nov 27th, flagged the POS software as malicious. Krebs On Security says the break-in was via a Target web server, which was used to deploy to an internal Target server, which deployed POS software to all of the US Target environment. According to later forensics, infected POS machines scraped credit and debit card magnetic stripe data as it was temporarily stored in machine memory. The malware accumulated data for 6 days while remaining undetected.
Dec 2nd: Malware Uploads Stolen Data
Based on analysis done by Seculert, Reedum/BlackPOS began transferring its stolen data (via a second compromised Target machine) to the FTP server of what appears to have been a hijacked website. This transmission occurred several times per day over a 2 week period. Also, beginning Dec 2nd, the attackers used a virtual private server located in Russia to download the stolen data from the FTP server. They continued to download this data for 2 weeks, eventually harvesting more than 1 gigabyte of sensitive customer data. FTP logs show that Target was the only retailer so affected, which implies the recent Neiman Marcus attack is unrelated to the Target breach.
Dec 11th: Forged Cards Selling on Black Market
Easy Solutions, a firm that tracks fraudulent card laundering noticed a 10-20 fold increase in high-value stolen cards on various black market forums, including cards from nearly every bank and credit union. Cards from the breach were being sold for $20 to $100 each.
Dec 13th: Krebs Breaks Story
Krebs On Security broke the story that Target was investigating a data breach potentially involving millions of records. Krebs reported that the breach began on Black Friday (close) and that investigators originally thought it extended to Dec 6th.
Dec 15th: Target Stops Data Transfer
This was the last day stolen data was transmitted to the compromised FTP server. It is also the date Target claims it was first sure of the breach, though they seemed to have been investigating it since at least the 13th, according to Kreb's sources. Target claims they had secured their environment by 6PM that evening. Target did not publicly announce the breach, though they notified credit card issuers during this time (from Rippleshot sources). While investigating, they also prepared their call centers for the public announcement.
Dec 18th: Symantec Adds Malware to Knowledge Base
Threat Expert (a Symantec web site) received a copy of the POS malware. Although currently removed from the site, a report on it has been saved. Symantec lists Infostealer.Reedum.B as being discovered on this date. We speculate this was uploaded from Target's investigation team.
Dec 19th: Target Announces 40M Cards Stolen
Target announced that 40M credit and debit cards were compromised between Nov 27th and Dec 15th. This info included customer names, card numbers, expiration dates, and card security codes (CVV). This makes the breach one of the largest in history.
Dec 20th: Target Offers 10% Christmas Discount
Target publicly apologized and offered a 10% discount to all shoppers who visit Target on Dec 21st and Dec 22nd. Based on our understanding of Target's volume, we estimate that this discount cost Target $36M.
Dec 23rd: Three Class Action Lawsuits
USAToday summarized 3 class action lawsuits with more than $5M in damages sought. Attorney generals of 4 states (CT, MA, NY, SD) have sought data from Target regarding the breach. The Secret Service was reported to be investigating the breach.
Dec 24th: Class Action Lawsuits Reach 15
CBS announced that the number of lawsuits had climbed to 15. Target admitted they are cooperating with the Department of Justice and the Secret Service. Target held a conference call with state attorney generals to bring them up to speed. Two US Senators (Richard Blumenthal of Connecticut and Chuck Schumer of New York) asked the US Federal Trade Commission to investigate the breach. Target's consumer perception scores dropped to their lowest level since 2007. Target's Buzz Score has dropped 45 points since before the breach (to -19). Citibank took 12 weeks and Sony 8 weeks to recover public perception after their breaches.
Dec 27th: Class Action Lawsuits Reach 40
At least 40 different lawsuits across the country had been filed against Target as of this date.
Jan 8th: Target Announces 70M More Compromised Accounts
Target announced that an additional 70 million people have been affected, including names, mailing addresses, phone numbers, email. Although there is overlap between the original 40M and the additional 70M, Target had not announced the extent of said overlap. Even if the overlap is large, this means that at least 70M people have had their information compromised, which is something like 45% of all card-holding consumers (160M). As of this writing, we do not know if this additional data was harvested via the same Reedum attack or in another way. With this announcement, Target likely surpassed the largest previous merchant breach: TJ Maxx's 46M accounts in 2007. Target's breach approaches the size of the largest breach of all time: Heartland Payment Systems saw 130M credit card numbers stolen in 2009. We learned that Target had been working with Verizon forensics and Mandiant (specializing in data breach recovery and recently acquired by FireEye for $1.1B). Although Target announced immediately after the breach that customers' payment information was encrypted and that the machines with the encryption keys were not part of the breach, Jan 8th saw the announcement that the keys were 3DES, which are known to be vulnerable to brute force cryptographic attacks. Hackers were able to bypass 3DES encryption in last year's Adobe exposure. 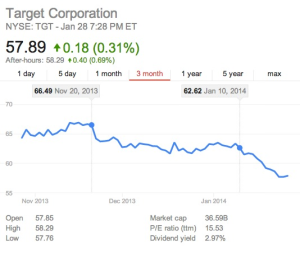
Jan 10th: Target Share Prices Plunge
Although Target share prices had held relatively steady since the initial damage after the breach announcement, the addition of 70M more accounts sent Target shares dramatically downward to almost 13% off from its Nov 20th peak. (Target will announce their Q4 numbers on Feb 26th.) The same day, Target announced the closing of 8 stores. Further, Target predicted its Q4 adjusted earnings per share would drop 20%. It claimed a 2.5% drop in sales during this quarter.
Jan 13th: Target Offers Whole US Free Credit Monitoring
Target CEO/President Gregg Steinhafel was interviewed on CNBC. "No one screens my email. So I have read every single email that has come to me." However, Target announced its shopping volume had nearly returned to normal as of this date. Target sent an email to most US consumers offering free credit monitoring and identity theft protection through Experian's ProtectMyID, which normally sells for $16/month. Consumers must sign up by April 23rd. Assuming Target gets a really excellent deal at $30/person/year and only 10% of consumers sign up for this service, Target would be on the hook for almost $400M. Although an excellent good-faith effort, many complain about the poor quality or irrelevance of this service.
Jan 15th: Class Action Lawsuits Reach 68
Class action lawsuits against Target climbed to 68 as of this date, from 21 states.
Jan 16th: Target Announces Data Breach Extends to Past 10 Years
And if you thought the breach could not get worse, Target announced that the compromised data extends far back in time, to as long ago as a decade.
Jan 19th: Malware Author Is Identified
IntelTrawler identified the author of BlackPOS as Sergey Taraspoc, a Russian 17-year old. Taraspoc reportedly sold this software on black market forums for $2000 to dozens of cybercriminals in Easter Europe and other countries. Note that this does not mean that Taraspoc was the perpetrator of the Target compromise, merely that he may have written the original software modified to perpetrate the breach. Russian Security firm Groupd IB claimed the BlackPOS malware has been used on “customers of major US banks, such as such as Chase (Newark, Delaware), Capital One (Virginia, Richmond), Citibank (South Dakota), Union Bank of California (California, San Diego), Nordstrom FSB Debit (Scottsdale, Arizona)." The Reedum version used at Target was specifically modified to avoid detection.
Jan 27th: Public Opinion On Data Security Mixed
An Associated Press - GfK Poll revealed that half of Americans were extremely concerned about purchases at stores involved in the breach. However, just 37% have used cash instead, and only 41% have checked their credit report. At the same time, state laws on when companies must reveal details of a data breach are inconsistent and often vague. This story will have legs for months or years: check back here as we summarize more.
March 5th: Target's CIO Resigns
The New York Times reported that Target’s CIO and executive vice president for technology services, Beth M. Jacob had resigned. This would be the first high-level executive to resign after the retailer's massive data breach affecting at least 70M people. Target would later announce that Jacob would be replaced by Bob DeRodes.
May 5th: CEO Resigns From Company
Nearly 2 months after Target's CIO resigned in early March, the chief executive officer of Target, Gregg Steinhafel, announced his resignation from the company. Reports stated that after discussions between Steinhafel and the Board of Directors, the board announced on Monday, May 5th that it had determined that Target required new leadership.
May 21st: Target Declines to Predict Total Costs of Data Breach Response
When Target filed its Form 8-K on May 21st, it said it could not predict the total costs required to respond to the massive payment card data breach. Rippleshot CTO, Randal Cox, broke down the estimated costs for the Target data breach and believes Target could end up paying $2.6B after the dust settles.
July 1st: Class Action Lawsuit Set for Trial
Top Class Actions reports that to date over 68 class action lawsuits have been consolidated in the U.S District Court of Minnesota over claims that the retailer failed to protect customer’s financial data. U.S District Judge Paul Maguson set an August 25th deadline for customers to file a consolidated complaint. It is estimated that as many as 100 cases could potentially join this litigation. All motions to dismiss must be filed by October 1st, while all who wish to join the litigation must file motions by December 1st. Class Certification motions will begin in April 2015, and the case must be ready for trial by April 1st, 2016, according to the Order.
July 31st: Target Names New CEO Following Breach
A former PepsiCo executive , Brian Cornell, has been named the new chairman and CEO of Target Corp. Ensuring Target's customers that the protection of their personal information is a top priority will be paramount for Cornell's first task as chairman and CEO. Jeffrey Roman of DataBreachToday goes into more detail of the big box retailer's newest executive hire.

