Solving ATM fraud has become a 2 billion-dollar question. (The impact of ATM skimming on a global scale). Getting to the bottom of ATM fraud means having a better understanding of how fraudsters think, how quickly they act and what payment channels they are targeting most.
In a recent webinar hosted by the ABA and Rippleshot's Chief Data Scientist Randal Cox, we discussed case studies of actual fraudster behavior and explored patterns of ATM misuse that help financial institutions fully understand the scope of this problem — and why it’s getting worse. [Catch the full webinar here].
Card skimming losses rose 70% between 2015 and 2016. That’s on top of the 546% increase seen in 2015. This rapidly-growing problem, Cox noted, is only getting worse. The difficulty with all types of fraud is the speed at which it evolves. ATM fraud, in particular, is evolving at a rapid pace. Banks are using new tools to fight fraud, but fraudsters are moving faster.
Banks typically have less than 48 hours after an ATM compromise before money is out the door. Banks need to quickly identify compromised ATMs and cards to get a handle on the scope of the problem — a process that can take weeks. Weeks isn't good enough when a problem needs to be solved in less than two days.
In the webinar, Cox explained into how Rippleshot’s automated fraud detection platform, Sonar — an ABA-endorsed solution — is helping issuers fight fraud better by identifying breaches at their source in order to detect them faster. It all comes down to studying spending patterns, he explained. After all, eventually all cards go fraudulent in one way or another.
“That natural decay of good cards against bad card gives us something to compare against,” Cox said. The key to an effective solution, however, is the ability to continually analyze card transactions; Rippleshot provides analysis at scale with millions of cards, every day.
With card fraud on the rise, ATM fraud is getting more attention — and rightfully so, Cox said, noting that “we hear again and again how bad the problem is, in particular for ATM skimmers.” When at ATM breach transpires, fraud occurs within 48 hours. From a typical breach, the end cost results can result in the loss of $250,000.
“It’s pretty painful to tell your board you’ve just lost a quarter of a million dollars over the weekend,” he said. “The problem is getting worse. As EMV has taken hold, the fraudsters have been looking around for the next low-hanging fruit and they have been paying attention to PIN fraud.”
Following the ATM Fraud Trail: Rippleshot’s Research
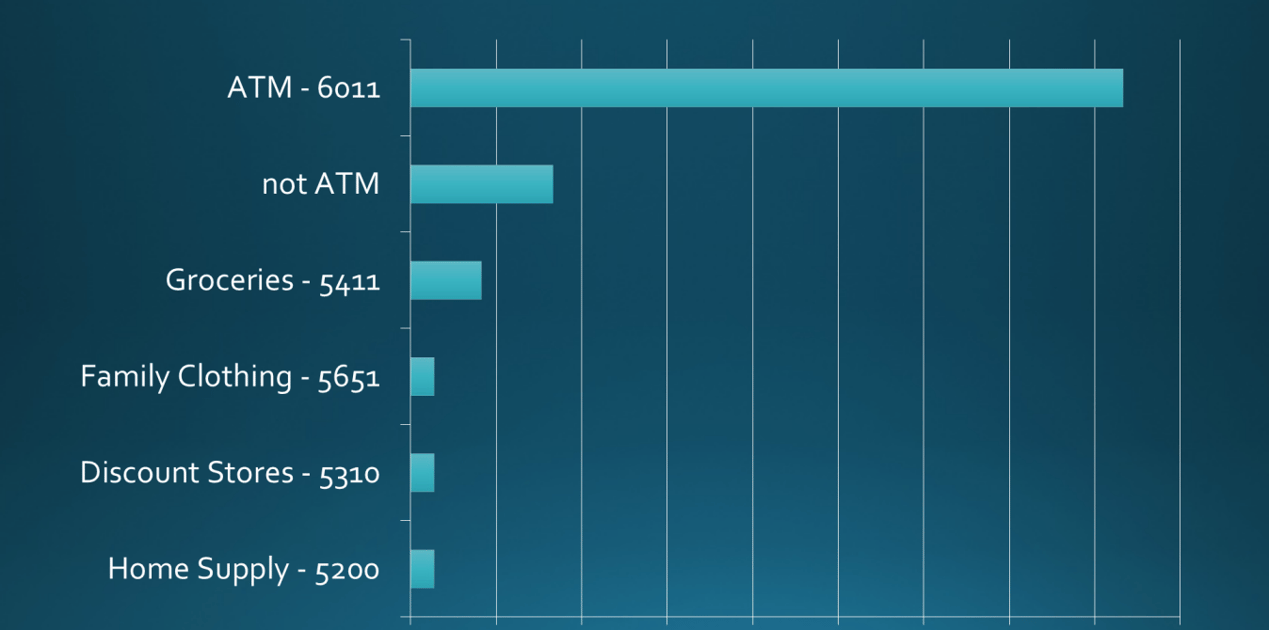
With almost invisible hardware sitting on ATMs, and fraudsters getting smarter, the problem is only going to be harder to play catch up with. This is especially true as PIN-related breaches expand far beyond ATMs and impact payment terminals at grocery stores and other merchants. To study how this problem is evolving, Cox did research on a mid-sized bank (250K cards) with PIN-related and PIN cashout breaches.
By analyzing a year’s worth of data, Cox was able to discover that the bank had 37 PIN-related breaches, 188 fraudulent cards. 2,645 at-risk cards and 673 fraud locations. And that’s just one use case for why ATM fraud continues to be a growing problem needing to be addressed.
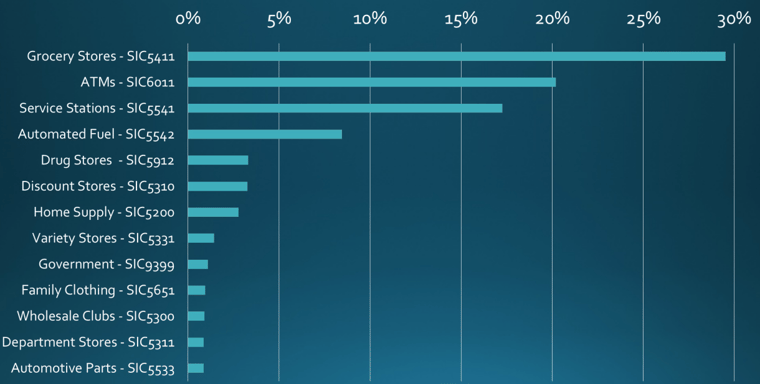
What industry data has shown is PIN-based card fraud is rising the quickest at ATMs. Although ATMs account for the most PIN-based fraud, grocery stores are gaining ground.
The reason grocery store PIN-based card fraud is likely to rise? The percentage of PINs entered at checkout is an indicator of where fraudsters might turn their attention toward.
Rippleshot’s Case Study: $110K Saved
Banks typically have less than 48 hours after an ATM compromise before money is out the door. Banks need to quickly identify compromised ATMs and cards to get a handle on the scope of the problem — a process that can take weeks. CAMS alerts, for example, are too late 70 percent of the time, Cox said. In fact, the alerts are only available after the threat has subsided. What’s needed for banks is a solution that detect ATM fraud within hours. That’s the only way to get ahead of the problem before the fraud spreads.
“PIN breaches occur incredibly fast,” Cox said. “Often you only have the day to respond. ...Most breaches run for just a week or two. ...Fraudsters have learned to move through your location at a rate that’s difficult to stop.” (Meaning that alerts that take weeks are already too late).
With Sonar ATM Fraud Detect, we were able to find three ATM skimmers and nearly 400 compromised cards for a regional bank were detected in about two hours. The end result? The bank reset compromised card PINs within 24 hours, stopping an estimated $110,000 of fraud, slashing reissuance costs, and lessening customer disturbance.
Sonar ATM Fraud Detect enables a quick-launch ability and minimal data requirements, ATM Fraud Detect processes data in near real-time to equip fraud teams with actionable activity reports in as little as two hours. ATM Fraud Detect provides card issuers with reports on potentially compromised ATMs and cards. Armed with this knowledge, fraud teams can take action faster on the affected cards — reducing fraud losses and client impact.

