
While the breadth of data being stolen in breaches has reached critical mass, the most valuable still remains payment card data - which is why many hackers still target it directly. Wondering how they do it? Follow along as we dive into the different ways fraudsters steal card information and how they then use it.
What Data Are They Stealing
Track Data
Every payment card has at least two tracks of data on its magnetic stripe. There is sometimes a third track, though it’s rarely used. Both tracks hold enough data to process a transaction, and most POS terminals are programmed to read both tracks, in case one is damaged.
Track one provides a bit more data - the account holder’s name and the format code, which will tell you whether or not it has come from a bank.
Track 1 Data (courtesy of Authorize.net)
|
Field Name |
Length |
Comments |
||
|
Start Sentinel (SS) |
1 character |
Indicates the beginning of Track 1; set to "%" |
||
|
Format Code (FC) |
1 character |
Indicates the card type; "B" indicates a credit/debit card |
||
|
Primary Account Number (PAN) |
up to 19 digits |
Always numerical; usually set to the credit/debit card number |
||
|
Field Separator (FS) |
1 character |
Delimits Track 1 fields; set to "^" |
||
|
Name |
2-26 characters |
Account holder's name |
||
|
Field Separator (FS) |
1 character |
Delimits Track 1 fields; set to "^" |
||
|
Expiration Date (ED) |
4 digits |
Always in the format MMYY |
||
|
Service Code (SC) |
3 digits |
Indicates what types of charges can be accepted |
||
|
Discretionary Data (DD) |
Variable* |
Determined by card issuer--may include Card Code and/or PINs |
||
|
End Sentinel (ES) |
1 character |
Indicates the end of Track 1; set to "?" |
||
|
Longitude Redundancy Check (LRC) |
1 character |
Used to verify that Track 1 was read accurately |
Track 2 Data
|
Field Name |
Length |
Comments |
||
|
Start Sentinel (SS) |
1 character |
Indicates the beginning of Track 2; set to ";" |
||
|
Primary Account Number (PAN) |
up to 19 digits |
Always numerical; usually set to the credit/debit card number |
||
|
Field Separator (FS) |
1 character |
Delimits Track 2 fields; set to "=" |
||
|
Expiration Date (ED) |
4 digits |
Always in the format MMYY |
||
|
Service Code (SC) |
3 digits |
Indicates what types of charges can be accepted |
||
|
Discretionary Data (DD) |
Variable* |
Determined by card issuer--may include Card Code and/or PINs |
||
|
End Sentinel (ES) |
1 character |
Indicates the end of Track 2; set to "?" |
||
|
Longitude Redundancy Check (LRC) |
1 character |
Used to verify that Track 2 was read accurately |
E-Commerce Data
Far less information can be stolen from online transactions, which prevents card data hijacked in this manner from being used in a card present situation. It does, however, still allow for fraudsters to use it for continued online purchases.
Data Typically Available:
Account Holder Name
Address
Card Type
Card Account Number
Expiration Date
CVC (Card Verification Code)
How They’re Stealing It
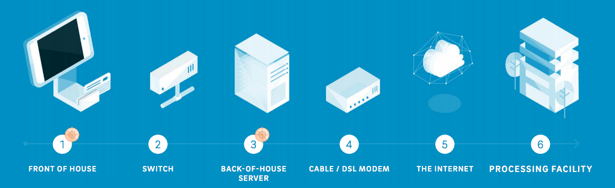
Track data is typically being stolen in two primary places - either the storefront POS terminals, or at a centralized back of house server where transaction data is stored (graphic courtesy of Trustwave Global Security Report).
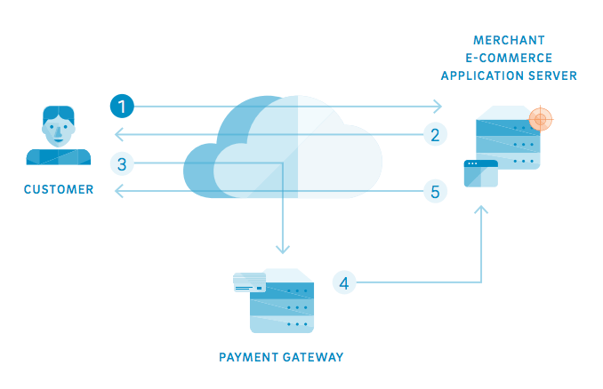
For e-commerce transactions, the data is typically stolen from the application server where customer information is stored.
In our How Cybercriminals Can Steal Your Credit Card Data post, we cover five different scenarios where card data can be stolen.
What They’re Doing With It After
Track data is far and away the most valuable information to steal, as there are a couple ways hackers can profit from the stolen it. The most obvious is to take the information and sell it on the underground market. But another option that can only be done with track data is to take the information and write it onto another card, which can then be used just like the original one. The technology required to do this is incredibly easy and relatively inexpensive for hackers to acquire. This video from WIRED shows you exactly how it’s done.
E-commerce data can be sold on the underground market as well, though it's far less valuable than track data. It can also be used to make purchases, but only online, as there isn’t enough information available to clone a card.
The quickly approaching switch to EMV will have a large impact on the way hackers steal this information, but is highly unlikely to prevent it altogether. Rather, it will just shift to other areas - and if we follow the path set forward by Europe and Canada in their implementations, e-commerce (card-not-present) fraud is set to see a massive boom in response.
To learn more about how the EMV implementation will affect credit and debit card fraud, check out our whitepaper below:


