Bad news. Ransomware is back with a newfound vengeance. Many of us know ransomware to be a notorious form of malware that prevents users from accessing their own systems, either by locking a user from a system entirely (locker ransomware), or encrypting user files on an affected system (crypto-ransomware). In either case, users are forced to pay a ransom in order to restore functionality and access, many times to the tune of thousands of dollars. Although ransomware dates back to 1989, its practice has ebbed and flowed in its prevalence over the years. However, it is clear that 2016 has seen a marked increase in the frequency, cost, and effectiveness of ransomware incidents. Follow the Rippleshot Team as we document the return of ransomware and its impact on the cybersecurity landscape of 2016.
Background
The origins of ransomware trace back to the AIDS Trojan, or PC Cyborg, devised by Harvard-trained biologist Joseph Popp. At the World Health Organization’s AIDS Conference, 20,000 attendees received a floppy disk (remember those?) containing the ransomware, labelled “AIDS Information- Introductory Diskettes”. Through symmetric cryptography, the Trojan virus would generate a series of hidden directories, decrypt file names, and display a message requesting a payment of $189 to the PC Cyborg Corporation. Although it was easy for decryption tools to recover the files, this seemingly innocent prank became the foundations for an entire criminal industry, and also made Popp the father of ransomware.
Gradual Evolution
It took 17 years for another notable strain of ransomware to be released, mostly because it was accompanied by a much higher level of sophistication, and also used asymmetric/ RSA encryption. Dubbed “Archiveus” in 2006, the Trojan malware encrypted all files in the MyDocuments directory. As an interesting plot twist, it did not ask for cash payment- instead, it asked for victims to buy medication from online pharmacies to receive a 30-digit password that decrypted the file system.
2012 marked the next pivotal trend in ransomware, with the development of the Reveton worm in Europe. Based on the Citadel Trojan, the ransomware would claim that an affected computer had been used for illegal purposes, and attempted to extort money in the form of a fraudulent criminal fine. A notice would inform a user of their crime, impersonate a law enforcement agency, and demand payment through an anonymous prepaid cash service such as Ukash, Paysafe, or MoneyPak.
Shortly after, CryptoLocker was born. Arguably one of the most revolutionary movements in ransomware history, CryptoLocker was the first cryptographic malware to spread by downloads from a website or email attachments sent to business professionals. It used AES-256 to encrypt files with specific extensions and delete the originals, and then uploaded a 2048-bit RSA key to a command-and-control server (C&C) in order to encrypt the AES-256 bit key. Hackers using CryptoLocker would then threaten to delete the private key if payment was not received within three days, making this an extremely formidable form of ransomware.
A Sudden Spike
As seen below, ransomware, especially crypto-ransomware, varied sharply in frequency over the years, but grew almost exponentially between 2013-2015.
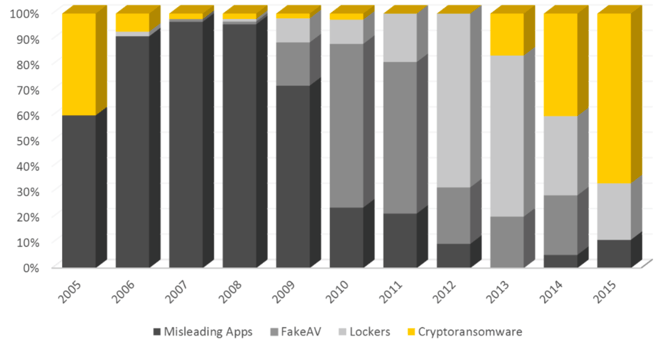
Why the sudden spike? The advent of the CryptoLocker mentioned earlier, and later CryptoDefense and CryptoWall, not only made it easier for ransomware to spread through websites and email attachments, but also made it easier for cyber gangs and hackers to accept payments (using Tor and Bitcoin).
The Return
Fast forward to now. The culmination of these ransomware developments over the years, along with many more, have set the stage for 2016. As CNN Money reported in April, cybercriminals collected $209 million in the first 3 months of 2016 alone, putting ransomware on pace to becoming a $1 billion criminal “industry” this year.
Even worse, ransomware attacks are becoming increasingly sophisticated, targeted, and expensive to victims. Thus far, 2016 has seen many high-profile ransomware attacks, including the Hollywood Presbyterian Medical Center (who paid $17,000 to restore services), the Methodist Hospital of Henderson, KY, and the MedStar hospital chain in March. Some say the estimates are even higher for unreported incidents of ransomware, with a recent report by Intel Security stating that the healthcare sector alone is experiencing 20 data loss incidents related to ransomware a day, and that over $100,000 has been made by hospital ransomware victims so far in 2016.
Also, March marked the first time ever that ransomware was deployed on a Mac. A time-delayed form of ransomware, KeRanger waits three days to begin the encryption process, and demands one bitcoin ($400) upon completion. Although Apple has ensured that the compromise does not occur again, the precedent has been set- and it is only a matter of time until more hackers crack the Mac security wall.
You’ve reached HackerCentral: How may I help you?
One of the biggest names in ransomware emerging in 2016 is Cerber. But it did not earn its name to fame by simply locking up files and blackmailing victims. Instead, it gained its reputation by providing top-notch "customer service". Ransomware is a tricky business, as it is estimated that only 50% of victims actually pay up, as some do not want to fund cybercriminals, others do not have the money, and most are not tech-savvy. Whatever the reason, extortionists have realized that providing customer service not only establishes trust and communication with their victims, but also ensures timely payment.
In a study conducted by F-Secure, the customer support services of various ransomware gangs were tested through an alias by the name of Christine. Christine discovered that ransomware deadlines could be extended three out of four times, and the ransom payment could be negotiated for a 29% discount on average. However, Cerber stole the show by providing the highest level of professionalism, a clean/ organized website, and quick response time.
The Solution
The market for ransomware is only poised to grow, as cybercrime-as-a-service businesses are flourishing, with more and more cyber criminals wanting to gain access to the ease and convenience of making money through the anonymous Internet. As potential victims, we must practice better “security hygiene” in order to prevent such attacks, either through simple solutions such as backing up our files and installing security, or becoming more educated as to what files to avoid opening. Regardless, it is clear that ransomware is here to stay.
To learn more about the state of payment fraud in 2016 and how to best protect consumers, check out Rippleshot’s white paper below: