Earlier this week, Verizon released their annual security report, 2015 Data Breach Investigations Report. With the help of 70 organizations from around the world, the 2015 Data Breach Investigations Report (DBIR) provides unparalleled insight into the various threats and security incidents that have plagued organizations of all sizes. We’ve put together some of the key takeaways from the DBIR to highlight some of the major trends ranging from attack methods to the latest data breach trends.
Victim Demographics
Before getting into the meat and bones of the DBIR, it’s important to understand the demographics behind those affected by data breaches and other security incidents. With the contributions of 70 additional organizations, the 2015 DBIR covered nearly 80,000 security incidents in 61 countries. Verizon points out that when compared to the 2014 DBIR, the total number of affected countries was much higher at 95.
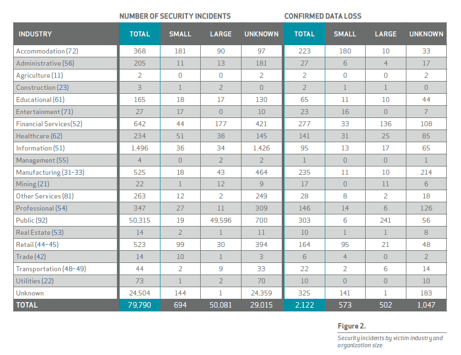
In the figure above, we can see that the five most affected industries; Public, Information, Financial Services, Manufacturing and Retail have seen the most security incidents and instances of confirmed data loss. Verizon points out that the higher number of security incidents for the Public sector coincides with the amount of participating governmental agencies in the report.
Data Breach Trends
In 2014, we experienced what many considered “the year of the data breach." As issuers continue to struggle with the rising tide of fraud losses, breached merchants are most often swept under the rug within six months. Many security experts believe that every single payment card in the U.S. has been exposed at some point due to data breaches. In 2014, the New York Times wrote more than 700 articles related to data breaches when compared to 2013. Before diving too deep into the DBIR, Verizon announced that the company had made some minor tweaks to their long-term findings that are worth addressing.
Hackers Increasingly Have More Than One Motive and Method of Attack
In the 2014 DBIR, Verizon added an additional motive to their Vocabulary for Event Recording and Incident Sharing (VERIS) called “secondary” to better track incidents where hackers had more than one motive to carry out their attacks. These secondary incidents occur when hackers target one victim as a way to target another victim using a different attack.
Verizon provides us with a possible scenario involving strategic web compromises. In this scenario, a hacker attacks a website to install malicious software with the hope that the hacker’s true target, the visitors of said website would download the malware. When accounting for the secondary incidents in this year’s report, nearly 70% of the attacks where a motive for the attack was found, included a secondary victim.
The Use of Memory Scraping
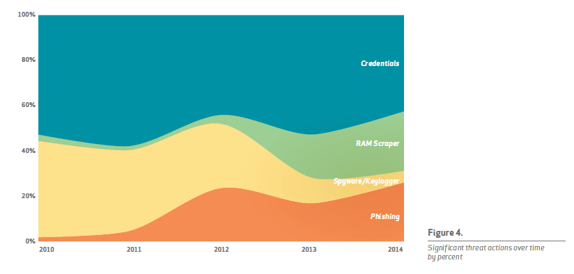
When looking Figure 4, we can see a shift in what ways malware has been implemented over the past five years. In 2010, nearly all of threat actions that were tracked used either illegally obtained credentials or through the use of spyware or a keylogger. Fast forward to the beginning of 2015 and we can see that the use of RAM or memory scraping has increased dramatically. Some of the more high-profile data breaches including the ones that hit Target and Neiman Marcus, could be traced back to RAM scrapers targeting each retailer’s point-of-sale systems.
People Still Fall For Phishing Attacks
Another form of threat actions also saw consistent growth over the past five years and unfortunately, we as consumers continue to fall for various forms of social engineering. We’ve all experienced the various phishing emails and phone calls asking to verify our sensitive account or payment information. And while the majority of us would claim to avoid falling victim to this threat action, Verizon’s report found evidence supporting the opposite.
According to the DBIR, 23% of phishing email recipient opened the fraudulent email and 11% clicked on various attachments. Verizon found that when a phishing campaign was created with just 10 emails being sent out, the hacker could expect at least one person will fall victim to the social engineering.
Software Vulnerabilities From Past Still Unpatched
As the dust began to settle following Home Depot’s data breach, which compromised as many as 56 million of its customers’ credit and debit cards, new reports came out from ex-employees of Home Depot stating that company’s security standards were not up to par. In a New York Times article, former IT security employees at the home improvement retailer said that the retailer relied on anti-virus software from 2007 to ‘protect its network’.
Thanks to the research put together by Verizon and Risk I/O, understanding how hackers exploit various software vulnerabilities and why these exploits continue to go unpatched becomes a little clearer. Aggregating vulnerability exploit data going back as far as 2013, Risk I/O compiled over 200 million successful exploits across 500+ common vulnerabilities and exposures (CVEs). This data set comes from more than 20,000 enterprises from 150 countries across the globe.
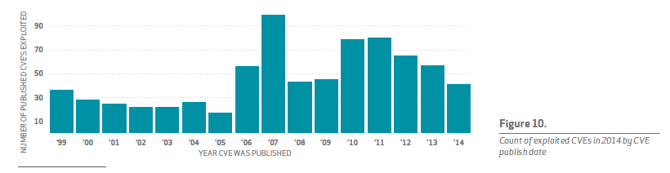
Based on the data set, 99.9% of the exploited vulnerabilities had been compromised for more than year after the associated CVE was published. In Figure 10, we can see that total number of CVE’s from at least year out since published covered old exploits that are so successful that hackers consistently go back to them.
Malware
With a reported 170 million for the total number of malware events in the past year, Verizon was able to determine that every second, five malware events occur. For example, those in the financial services industry experienced on average 350 malware events every week for the past year. Even more shocking, organizations in the education industry experienced 2,332 malware events each week.
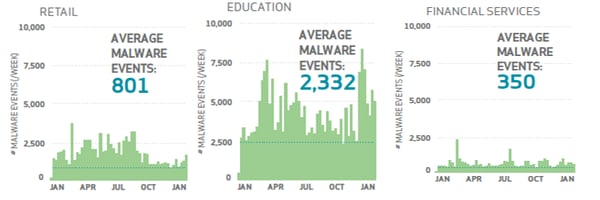
Verizon offered some possible explanations as to why these figures are so polarizing. When looking at the financial services industry, enhanced security policies and software could help in the reduction of phishing emails received along with the increased training that employees in the financial services industry undergo. The opposite could be said for those in the education industry due to the sheer volume of potential victims.
Conclusion
What we’ve just covered in this recap of Verizon’s 2015 Data Breach Investigation Report barely scratches the surface of this comprehensive report. There are so many great stats and figures in this year’s report, (be sure to check out Figure 19) that we couldn’t include in this blog post without rewriting the entire report ourselves! We encourage you to download a copy for yourself, and hopefully you’ll find all the pop culture references as funny as we did.
We are getting closer and closer to the EMV implementation in the U.S. But what does the deadline mean for issuers, merchants, and consumers? Download our latest white paper EMV Adoption In The U.S.



