
We have a good idea of the short-term consequences of data breaches- lawsuits, chargebacks, etc. But what about the long-term? A recent research report published by Claire Greene and Joanna Stavins of the Federal Reserve Bank of Boston sought to find a conclusive answer, leveraging consumer perceptions surrounding Target’s data breach as a case study. By examining longitudinal data on 1,908 US adults from results of the Survey of Consumer Payment Choice (SCPC), the report took advantage of a naturally ripe environment for experimentation, as some respondents were asked to rate payment instrument security before the Target data breach became public knowledge, and others answered the survey after news of the breach became widespread. Although the research has merit in identifying the inelastic behavior of consumers regarding payment instrument usage, it fails to address how data breaches contribute to costly card-reissuance and false-positive declines for banks and credit unions.
Breaches and Consumer Perceptions
Titled Did the Target Data Breach Change Consumer Assessments of Payment Card Security?, the report primarily addressed the following questions:
- In the short term, did consumers who answered after the breach was announced (Group 2) rate payment instrument security differently from consumers who answered before the breach (Group 1)?
- In prior responses on earlier surveys, did respondents who later constituted Group 1 rate the security of payment instruments differently from those who later constituted Group 2?
- Are there demographic differences between the two groups that could be correlated with their ratings of payment instrument security?
- In the longer run, did consumers’ ratings and use of payment instruments change between the fall of 2013 (before the breach) and the fall of 2014?
After controlling for the compounding effects of demographic differences between Group 1 and Group 2 through regression analysis, evidence from the research suggested that ratings for the security of debit cards in safeguarding personal information (PI) by Group 2 were significantly worse than such ratings by Group 1, or those who responded before the breach was widely known. On average, the rating on the security of personal information of debit cards relative to the rating on the security of other payment instruments was 11.3 percent lower shortly after the Target breach. From this data, one can conclude that widely publicized data breaches do indeed have the potential of shifting consumer perceptions of payment security.
Actions Speak Louder than Words
Intuitively, one would expect a noticeable decline in debit card usage after a data breach announcement due to doubtful sentiments about payment security. Surprisingly, however, the report found no statistically significant differences in the adoption or shares of payment instrument use for debit cards between 2013 and 2014, implying that consumer payment behavior in the long-term aggregate is not significantly impacted by fleeting perceptions.
So Everything's Fine then...Right?
So if consumer behavior is unaffected by data breaches, as a bank or credit union, I have nothing to worry about, right?
Wrong.
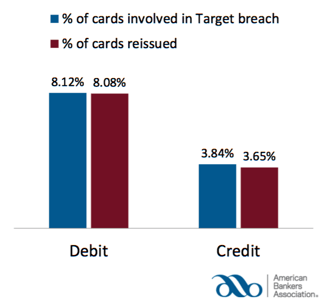
Even if customers are continuing to spend money on payment cards after big-scale data breaches, card re-issuance will persist as a problem because issuing institutions will reactively send customers new cards in the mail when they believe that old ones have been compromised. Not only is this process incredibly ineffective in terms of cost, it has profound long-term consequences as well. Circling back to the Target data breach discussion, a Target Breach Impact Survey by the American Banker’s Association (ABA) revealed that 8.12% of debit cards were possibly involved in the data breach, and 8.08% of cards were re-issued, meaning that the vast majority of cards believed to be compromised were re-issued.
Now, look at the percentage of debit cards that actually resulted in fraud loss:

Less than 1% (.64% to be exact) of debit cards actually saw fraudulent activity! In Rippleshot’s experience, only 1-2% of these affected cards would have gone fraudulent. This means that a whole lot of customers are getting new cards when they don’t need to.
What’s scary about this? Well, besides for the fact that the average cost for reissuing is $9.72 per debit card, one of our sources at MasterCard told us that 20% of re-issued cards never get reactivated. We’re talking millions of dollars of revenue lost.
Check the Back of Your Wallet
If this wasn’t bad enough, an even larger issue at the core of data breaches is customer disturbances. When data breaches occur, financial institutions are quick to fortify their decline rules, causing more false-positive declines to customers. False-positives are transactions that are wrongly declined due to suspected fraud, and can seriously erode customer loyalty over time. Customers hate false positives, as they generally aren’t aware of what’s happening behind the scenes, and largely don’t care- they will continue to blame merchants and financial institutions. In a 2015 study, Javelin estimated that 15% of all cardholders had at least one transaction incorrectly declined in the past year, and nearly 4 in 10 (39%) declined cardholders reported that they abandoned their card after being falsely declined.
Therefore, since negative perceptions on payment security are short-lived, data breaches won’t interfere with payment card usage significantly, but they will certainly have long-term repercussions in the form of unnecessary card re-issuance and an overall reduction in customer loyalty.
Learn more about how unnecessary card re-issuance and false declines are costing financial institutions millions in our latest white paper- 2016 Industry Report: False Positives and Card Reissuance



