The landscape of fraud between 2015 to 2016 is best characterized as uncertain and dynamic. As government institutions such as the CFPB and FFIEC begin to play a bigger role in cybersecurity regulation, it has yet to be seen what data security protocols will be required of financial institutions. Also, pending legislation in Congress surrounding data security has the potential to determine federal standards of information security for merchants. Finally, with back-and-forth lawsuits between retailers, payment card networks, and issuers over disputes regarding EMV compliance and liability shift, nobody is exactly sure who will come out on top.
At Rippleshot, we understand how difficult it can be to juggle so many moving parts and develop actionable insights from them. That’s why we created a timeline for you to get up to speed on recent developments in card fraud and payments security.
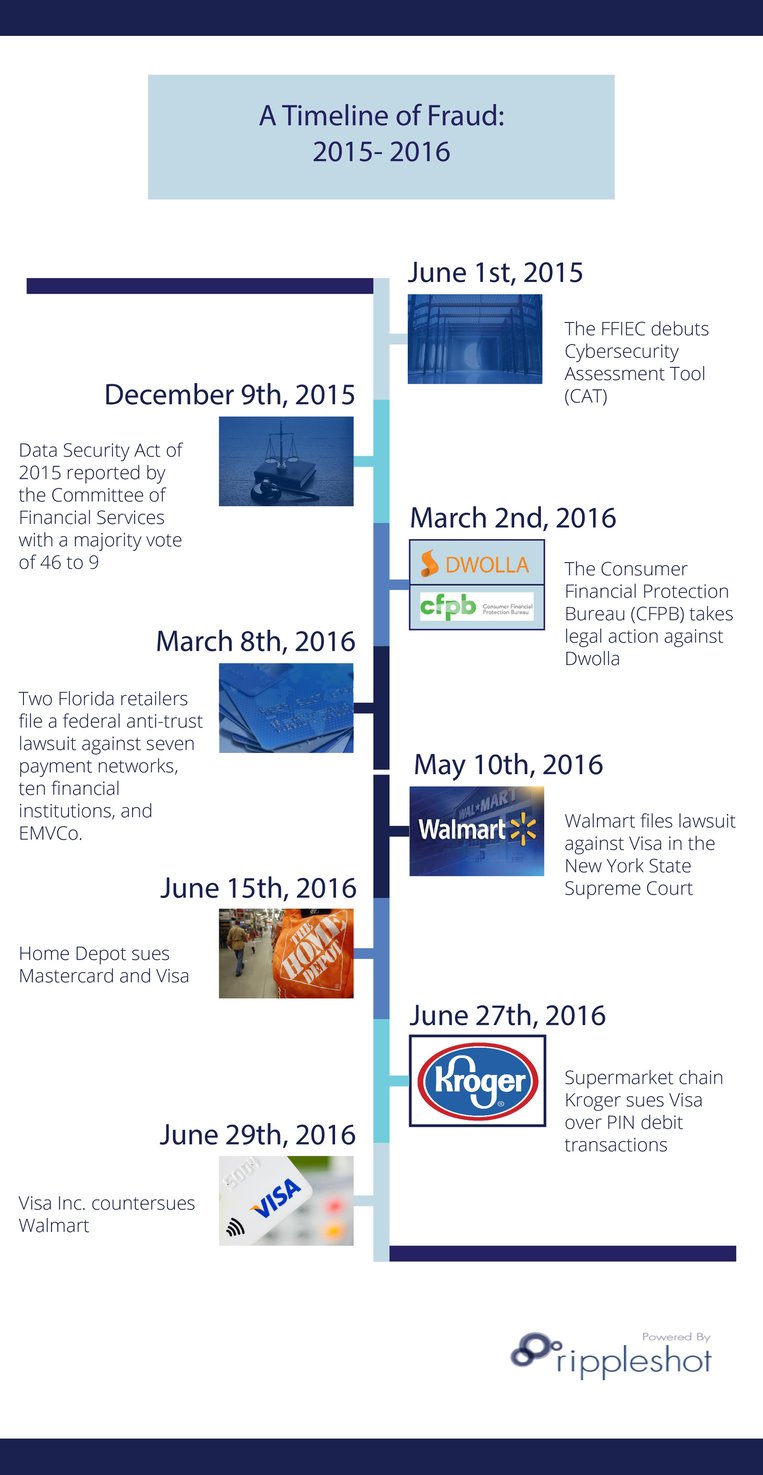
June 1st, 2015
In June of 2015, the Federal Financial Institutions Examinations Council (FFIEC) debuted the Cybersecurity Assessment Tool, commonly known as CAT. As a federal interagency body responsible for creating standard assessments and examinations for all financial institutions, the FFIEC developed CAT to help institutions identify their risks and determine their cybersecurity preparedness in light of the increasing number and sophistication of cyber threats. The CAT can be summarized into two primary parts:
- The Risk Profile Assessment, which is a series of questions that financial institutions must answer about their own internal operations, which then leads to the determination of an inherent risk profile - from least to most.
- The Cybersecurity Maturity Guidelines - A set of cybersecurity recommendations, laid out by risk profile, that escalate in terms of requirements, as the risk profile increases.
December 9th, 2015
On December 9th, 2015, the Data Security Act of 2015 was reported by the Committee of Financial Services with a majority vote of 46 to 9. Essentially, the bipartisan bill requires merchants that handle sensitive financial account information or nonpublic personal information to implement an information security program and notify consumers, federal law enforcement, payment card networks, and consumer reporting agencies of data breaches containing unencrypted sensitive information. Other salient provisions include directing entities to require third-party service providers (generally point-of-sale) by contract to implement appropriate safeguards, allowing financial institutions to disclose information with account holders regarding breaches, and expanding compliance procedures for financial institutions under the Gramm-Leach-Bliley-Act (GLBA) to businesses and retailers.
March 2nd, 2016
Early in March 2016, the CFPB (Consumer Financial Protection Bureau) took action against payment platform Dwolla for misinforming consumers regarding the security of their data. Ultimately, the result was $100,000 in penalties against Dwolla, along with an order to fix any security weaknesses in their systems, put in place and train employees on comprehensive data security policies, and perform consistent risk assessments and audits.
This is the first foray the CFPB has made into the data security space, putting the industry on edge. The court decision puts the focus back on how organizations with access to consumer data are ensuring its security, and also highlights the broad reach given to the CFPB as defined by the Dodd-Frank act.
March 8th, 2016
Two Florida retailers, B&R Supermarket Inc and Grove Liquors LLC, filed a federal anti-trust lawsuit against seven payment networks, ten financial institutions, and EMVCo., claiming that the defendants conspired together to create a liability-shift date they knew retailers could not meet.
In the lawsuit, both retail chains advance the theory that the defendants knowingly imposed an EMV deadline that most merchants could not meet, in an effort to transfer losses for fraud stemming from counterfeit and lost-and-stolen cards to merchants. Retailers have faced much adversity in meeting the requirements by the liability shift date due to a backup in getting chip-enabled POS terminals certified, a process that is largely out of their control, leaving them helpless against a wave of chargebacks that they found themselves suddenly responsible for “overnight.”
May 10th, 2016
On May 10th, 2016, Walmart Inc. sued Visa, claiming that the payment card network demanded that Walmart use “fraud prone” verification, signatures instead of PINS, because Visa stands to make more money processing. As Walmart spokesman Randy Hargrove puts it, “PIN is the only truly secure form of cardholder verification in the marketplace today, and it offers superior security to our customers”. He added, "Visa has acknowledged in many other countries that chip-and-pin offer greater security. Visa nevertheless has demanded that we allow fraud-prone signature verification for debit transactions in our U.S. stores because Visa stands to make more money processing those transactions."
June 15th, 2016
Mid-June of 2016, the DIY retailer Home Depot filed an antitrust lawsuit against Mastercard and Visa, accusing the payment networks of attempting to block the adoption of chip-and-PIN on credit card transactions following the migration to EMV payment security standards last October. The lawsuit, which was filed in the U.S. District Court for the northern district of Georgia, also charged Mastercard and Visa with conspiracy, suggesting that both enforced the less secure chip-and-signature standard because the networks stand to collect higher merchant fees for routing signature-based card transactions as opposed to PIN.
June 27th, 2016
Kroger Co. sued Visa Inc., alleging that the payment card network issued an ultimatum against Kroger Co., coaxing the retailer into accepting new chip-enabled debit cards without requiring PINs by threatening them with increased fees and denied debit acceptance capacity in-store.
Like Walmart, Kroger required customers to verify debit-card transactions by PIN, not by signature. However, the company said its dispute with Visa started after the card network said the setup of Kroger’s EMV terminals was not in compliance with its rules, which state that stores must give customers the choice between a PIN and a signature for verification purchases.
June 29th, 2016
Visa Inc. recently countersued Walmart, claiming that the retail giant secretly tested a system where no signature option was allowed with Visa debit cards. According to Reuters, Visa noticed a decline in debit card transactions after the store’s “PIN-only policy” was secretly instituted, and heard complaints from customers about not being able to use debit cards at Walmart without a PIN. In a public statement, Visa defended its claims by asserting, “Instead of complying with the terms of the commercial agreement that the two companies negotiated and agreed to in 2015, Walmart is attempting to avoid its obligation to provide a signature option for their customers when paying with a Visa debit card”.
Learn about the dynamic ecosystem of fraud in 2016 and develop actionable insights through our newest white paper, State of Card Fraud: 2016.